AlliedSecure
AIM 360-Degrees
- Requirement
- Solution
- Value Addition

Cyber security solutions and services
|
Assess
|
Implement
|
Manage
|
||
|
Security Architecture/
Compliance Audit |
Data Protection
|
Managed Security Service
|
||
|
Dark Web Analysis
|
Identity Management
|
Threat Management
|
||
|
Breach Attack Simulation
|
Application Security
|
Social Media and Brand Protection
|
||
|
Vulnerability Analysis/
Penetration Testing |
Network Security
|
Dynamic Deception
|
||
|
Red/Blue Team Simulation
|
Endpoint Security
|
SOC Tools
|
||
|
Email Protection
|
Advanced Incident Response
|
|||
|
Cloud Security
|
Cyber Forensics Analysis
|
|||
|
IOT Security
|
||||
SOC Models

Managed Security Service
|
||||||||
Our Partners

Compliant Infrastructure
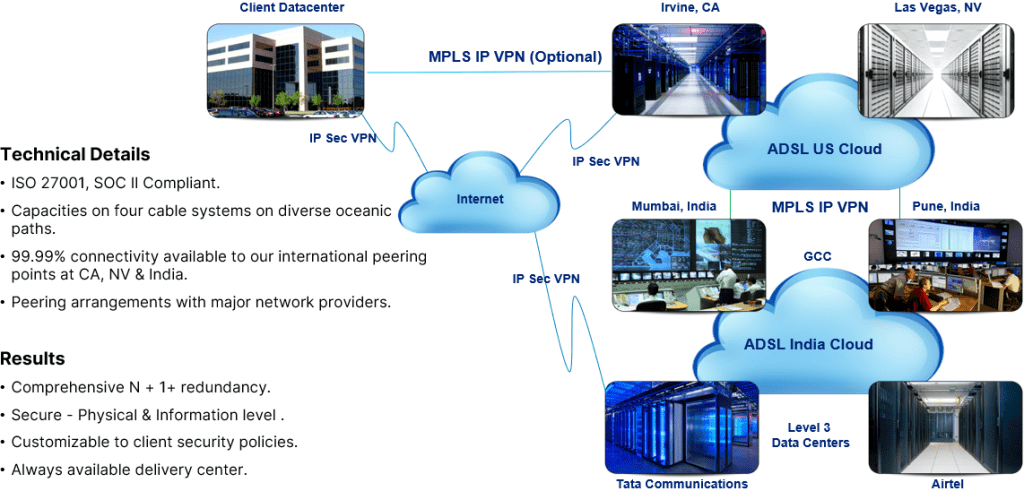
Cyber Threat Management
Threat Hunting and Management
- With access to research capabilities, know-how and threat intelligence repositories, our team can accurately identify external threats, prevent attacks, and ensure resilience.
- Continuously monitor Open, Deep and Dark web sites, as well as closed forums, social networks and messaging platforms and harvest data based on the organization’s predefined threat hunting requirements.
Dynamic Deception
Use Deception Techniques to Protect
- Use deceiving traps and lures designed to attract an attacker into engaging and getting away from production assets.
- Project decoy throughout the network along with endpoint credentials, mapped shares, deception data or applications that will breadcrumb the attacker back to an engagement server that will alert on the presence of an attacker.
- By laying a maze of decoys, lures, and mis-directions security teams can accurately and efficiently detect early reconnaissance, lateral movement, and credential theft, improving detection time and reducing attacker dwell time.
Security Incident Response and Forensics
Engagement Models
- Onsite Incident Response (Rapid Response Team).
- Remote Incident Support.
- Onsite/Remote Digital Forensics.
- Long term staffing contracts.
Summary of Service and Deliverables
- Incident Handling based on Industry Best CERT processes.
- Incident Preparation & Digital Forensics.
- Reverse Engineering & Malware Analysis.
- Lessons Learned document & Incident Reports.
- Support to Law Enforcement Agencies.
- Security Remediation Support.
- Create/Enhance Incident Handling Processes.
- Creating Incident Scenarios and Response Plan




Comments are closed.